History, Current Status and Future Scenarios of Expanded Password System
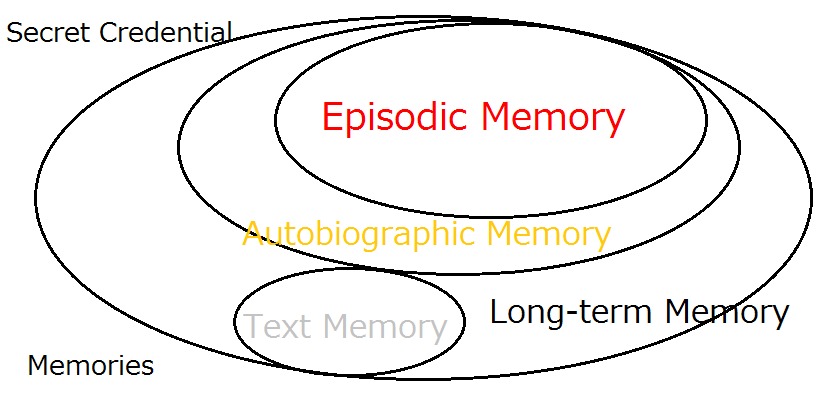
Predicament of Digital Identity
Passwords are so hard to manage that some people are urging the removal of passwords from digital identity altogether. What would happen, then, if the password is removed from our identity assurance?
Where the password was kicked out, security providers would be given only the physical token and the biometrics as security factors, whereas biometrics requires a fallback measure against false rejection. With the password removed, nothing but the token could be the fallback measure for the biometrics. Then system designer could have only the two choices as follows.
(1) authentication by the token alone, with an option of adding another token. Its security effect is highlighted in this cartoon we published14 years ago.
(2) authentication by the biometrics deployed in ‘multi-entrance’ method with the token as a fallback measure, security of which is lower than (1) irrespective of however called it may be, with an option of adding another token, as quantitatively explained here.
What a barren desert it would be!
More significantly, the password-less (will/volition-less authentication) is not consistent with the value of democracy. It would be a 1984-like Dystopia if our identity is authenticated without our knowledge or against our will.
Then What Else?
‘Achieving higher-security by removing the password’ and ‘Killing the password by password-dependent biometrics’ are both no more than the hyped myths. Then, what else can we look to as a valid solution to the predicament of digital identity?
The answer is expanding the password system to accept credentials based on our non-text memories as well as the text memories. We call this proposition ‘Expanded Password System’
![“Expanded Password System
Bans & Only I can select all of
BL] them correctly
Broader choices with both images and characters accepted
i
Easy 10 manage reletons between accounts and corresponding passwords.
&
Torturous login is hstory. Login is now comfortable, relaxing and heaing
SRO
250
8](https://contents.bebee.com/users/id/13855668/article/history-current-status-and-future-scenarios-of-expanded-password-system/83640d14.jpg)
By accepting non-text memories, especially images associated with autobiographic/episodic memories, the Expanded Password System is able to offer a number of excellent features as follows.
- It is not only stress-free for users but fun to use.
- It turns a low-entropy password into high-entropy authentication data
- It eases the burden of managing the relationship between accounts and passwords
- It deters phishing attacks with this unique feature.
https://www.linkedin.com/pulse/targetedspear-phishing-expanded-password-system-hitoshi-kokumai/
- It can be deployed under any type of circumstance, including, combat and other panicky situations.
https://www.slideshare.net/HitoshiKokumai/identity-assurance-in-emergencies
- It supports existing schemes, such as:
- - Biometrics which require passwords as a fallback means
- - Two/multi-factor authentications that require passwords as one of the factors
- - ID Federations such as password managers and single-sign-on services that require passwords as the master-password
- Simple pictorial/emoji-passwords and patterns-on-grid can be deployed on this platform.
- It is relevant whenever text passwords and pin numbers are in use
- And, nothing would be lost for people who want to keep using text passwords
- Last but not least, it continues to rely on free will.
History and Current Status
The concept of this Expanded Password System first came up in 2000. It was followed by the prototyping in 2001 and the commercial implementations from 2003. The history is outlined in this article – How Expanded Password System Got This Way - .
Actually, over the period of 2003 to 2008, the business grew successfully. We saw several commercial adoptions amounting to some US$1 million, even though handling images was a much heavier task in those days when CPU was slow, the bandwidth narrow and the storage expensive.
It then ceased to grow as people were more and more carried away by the myths of biometrics and password-less authentication which the advocates alleged would kill the passwords altogether, with our proposition included, although we knew that biometrics have to depend on the password as a fallback measure and that a password-less auathentication, if literally implemented, would only bring tragically insecure cyberspace..
After struggling in vain to fight back for several years, we chose to get out of Japan where biometrics vendors were far more dominant than anywhere else, and started to look for bigger chances worldwide. Now, we have a lot of friends and supporters globally. The writer was invited to speak at KuppingerCole's Consumer Identity World 2018 in Seattle and Amsterdam. Expanded Password System is now acknowledged as Draft Proposal' for OASIS Open Projects.
Well, as indicated in the above, we had come up with not just prototypes but also several commercial products developed for the Japanese market such as follows:
Client Software for
- Device Login (commercial implementation)
- Applications Login (prototype)
- Image-to-Code Conversion (p)
Server Software for
- Online-Access (c.i.)
- 2-Factor Scheme (c.i.)
- Open ID Compatible (p)
Data Encryption Software with on-the-fly key generation
- Single & Distributed Authority (c.i.)
None of them, however, are well suited for the services and sales on the global markets, since the programs were all written by Japanese engineers for the Japanese clients with no consideration about the operation, support and maintenance outside Japan.
This also means, however, that we will be able to come up with the products for the global market easily and quickly with a relatively small budget because all that we need to do is to re-write the software in English with the updated cryptography.
For a brief glimpse of what Expanded Password System can offer, please watching these brief videos.
Basic Operation - on Smartphone (1m41s)
High-Security Operation - local on PC (4m28s)
Capture and registration of pictures - mapping to long PIN Codes (1m26s)
The readers might also be interested in this comprehensive FAQ -
Future Scenarios
In view of the global nature of our enterprise, we are planning to set up the headquarters in an English-speaking country where we have easy access to the sufficient business and technological resources.
Identity/Security-related businesses who are interested to share the benefits of Expanded Password System could choose one or some of the scenarios as quoted below.
1. Become one of the co-founders of a new business entity that we are going to set up as the global headquarters.
2. Secure a highly privileged status by joining our team at OASIS Open Projects as a voting sponsorship member.
3. Secure some advantageous status by taking part in the active discussions at the OASIS Projects as a non-voting member.
4. Consider other scenarios depending on their aspiration and budget.
* All would depend on their judgement on
- how large or small the enterprise of the now-unknown Expanded Password System could grow and how long or short it could survive and sustain,
- as compared with the now-popular propositions such as ‘password-less authentication’, ‘biometrics as a password-killer’ and ‘physical tokens as a password-killer’,
- as a legitimate successor to the traditional seals, autographs and text-passwords, bearing it in mind that this enterprise could keep a value for long-term social good.
< Related Articles >
Digital Identity and Democracy
Hitoshi Kokumaiの記事
ブログを見る
Our password headache may well be the consequence of these dual causes - · ‘Use of Impracticable Pas ...

I take up this report today - “Facebook's metaverse plans labelled as 'dystopian' and 'a bad idea'” ...
Biometrics is 'probabilistic' by nature since it measures unpredictably variable body features of li ...
関連プロフェッショナル
この職種に興味がある方はこちら
-
獣医営業 - 東日本営業部(福島・栃木エリア)
次の場所にあります: Talent JP C2 - 5日前
Hill's Pet Nutrition Tokyo, 日本Relocation Assistance Offered Within Country · # 東京, Tokyo-To/東京, Japan/日本 · Colgate-Palmolive Companyについて · Colgate-Palmolive Companyは、人々、ペット、地球のより健康的な未来を追求する、革新的で思いやりにあふれた成長企業です。Colgate-Palmolive Companyは、オーラルケア、パーソナルケア、ホームケア、ペットフードという分野に注力しており、Colgate、Palmolive、elmex、hello、me ...
-

製造スタッフ
次の場所にあります: beBee S2 JP - 1週間前
株式会社綜合キャリアオプション さくら市, 日本 TEMPORARY株式会社綜合キャリアオプション(1314VJ0417G7★46-N) · \日勤夜勤選択OK♪/美味しいアイスクリームづくり★/日払いOK · ====仕事内容==== · アイスの製造、加工食品の製造業務 · ≪ミドルの転職≫ · 40代以上、ミドル層の幅広い年代の方が活躍しています · ≪女性が多い職場≫ · もちろん男性の応募もOKですよ · ≪プライベートが充実する≫ · 残業はほとんどナシ · 場合によってはお願いすることもあります♪ · ≪完全週休2日制≫ · 家族と友人と一緒にプライベート満喫 · ≪髪色自由で楽しい職場≫ · 明るすぎたり ...
-

スシロー富山中川原店
次の場所にあります: Talent JP C2 - 2日前
AKINDO SUSHIRO Toyama, 日本仕事情報 · ● 仕事内容 開店前のフロア清掃は、お客様をお迎えするにあたりとても大切 · なお仕事です。開店後は、お客様のご案内・お会計・お持ち帰り · 商品の受付と受け渡し等のお仕事があります。基本的に注文は · レーンから流すので、お寿司を運んだりすることはほとんどあり · ません閉店したら、片付けやレジ締めをしてもらいます。 ●大学生/専門学生、活躍中 学校生活では沢山の事を学び、沢山の方と出会うと思います。し · かし、学校の中だけでは分からないことも沢山ありますスシロ · ーでは、性別はモチロン、年齢も様々です。沢山の方と出会い、 · 一生 ...


コメント
Zacharias 🐝 Voulgaris
4年前 #7
Yes. It's a system I've developed over the years that is more secure than the current standard and immune to quantum cryptanalysis since it relies on complex systems theory rather than plain math. I've talked about it openly on one of my videos on the O'Reilly platform (aka Safari Books Online) and I'm open to sharing the source code with anyone who is up for providing me any feedback (it's written in Julia language). I'm quite interested in cryptanalysis myself and have studied it quite a bit, always with the use of a computer. I've managed to break several codes over the years and even created a video on the topic (also published on O'Reilly). Yet, despite all this, I've never managed to break the Thunderstorm code, while anyone who's ever seen it hasn't managed to pinpoint a weakness yet. That's not to say that it's perfect, however, which is why I never tried commercializing it.
Hitoshi Kokumai
4年前 #6
Likewise
Hitoshi Kokumai
4年前 #5
We would lose the future if we lose the secret credentials.
Zacharias 🐝 Voulgaris
4年前 #4
I can see how this image-based system, coupled with a powerful encryption method like Thunderstorm (a system I've devised that works with large keys in a very chaotic manner, making cryptanalysis exceptionally hard), could offer a new level of security, unfathomable by today's standards. Perhaps we can discuss a potential collaboration at one point, if you are interested. Cheers
Hitoshi Kokumai
4年前 #3
The password (secret credential) is absolute necessary in democratic societies. 'Text Password' is known to be insufficient. Then, if we think logically, trying something for 'Non-Text Password' is the only way forward.
Hitoshi Kokumai
4年前 #2
Digital identity could have a future without 'Text Password' but would not have the future without 'Password' or 'Secret Credentials'.
Zacharias 🐝 Voulgaris
4年前 #1