On Ruinous Misperception of Biometrics

Here are some of my recent writings about the misperception on security-ruining biometrics.
‘Not as secure as claimed’ is one thing. ‘Harmful to security’ is another.
Probabilistic Is Human Body, Not Pattern-Matching Algorithm
US Army appears tobe scarily misguided
AI-Enhanced Biometrics – How Dreadful?
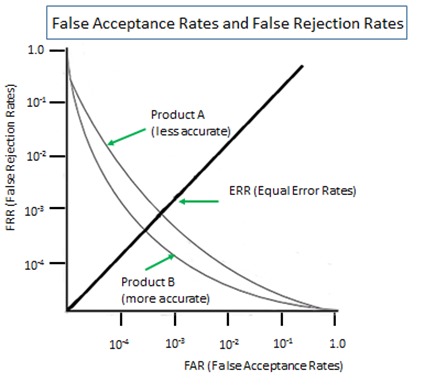
Quantitative Examination of Multiple Authenticator Deployment
It appears that there are so many security professionals who pay no attention to the exactly opposite effects of 'multi-layer' and 'multi-entrance deployments. ‘Multi-Layer’ is also represented by ‘In-Series’, ‘In-Addition-To’, ‘All/BothAnd’ and ‘Conjunction’ in logic, while ‘Multi-Entrance’ by ‘In-Parallel’, ‘In-Stead-Of’, ‘EitherOr’ and ‘Disjunction’. Let me offer a quantitative examination of multiple authenticators deployed in two different ways.
Vulnerability (attack surface) of an authenticator is generally presented as a figure between 0 and 1. The larger the figure is, the larger the attack surface is, i.e., the more vulnerable. Assume, for instance, as just a thought experiment, that the vulnerability of the PKI-enabled token (x) be 1/10,000 and that of the password (y) be 10 times more vulnerable, say. 1/1,000. When the two are deployed in ‘multi-layer’ method, the total vulnerability (attack surface) is the product of the two, say, (x) and (y) multiplied. The figure of 1/10,000,000 means it is 1,000 times more secure than (x) alone.
On the other hand, when the two are authenticators deployed in ‘multi-entrance’ method, the total vulnerability (attack surface) is obtained by (x) + (y) – (xy), approximately 0.0011. It is about 11 times less secure than (x) alone.
So long as the figures are below 1, whatever figures are given to (x) and (y), deployment of 2 authenticators in ‘multi-layer’ method brings higher security while ‘multi-entrance’ deployment brings lower security. As such ‘multi-layer’ and ‘multi-entrance’ must be distinctly separated when talking about security effects of multiple authenticators.
Remark: Some people may wonder why (xy) is deducted from the sum of (x)+(y).
When (x) and (y) is very small, the (xy) is very close to 0, which we can practically ignore. But we should not ignore it when the figures are considerably large.
Suppose a case that both the two authenticators are deployed in an extremely careless manner, for instance, that the attack surfaces of (x) and (y) reach 70% (0.7) and 60% (0.6) respectively. If simply added the figure would be 130% (1.3). It conflicts with the starting proposition the figures being between 0 and 1.
Imagine a white surface area. Painting 70% of it in black leaves 30% white surface. Painting 60% of the remaining 30% in black will result in 88% black and 12% white surfaces. Painting 60% first in black and then painting 70% of the remaining 40% brings the same result of 88% black and 12% white. So does “(x)+(y)-(xy)”. The overall vulnerability (attack surface) is 0.88 (88%) in this case.
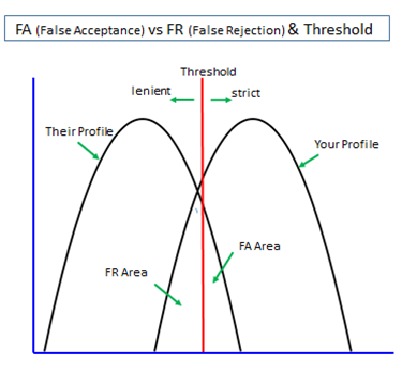
The same calculation applies to biometrics used in cyber space where it has to rely on a fallback password/PIN deployed in ‘multi-entrance’ method against false rejection. You might assume that biometrics deployed with a password/PIN in ‘multi-layer’ method should bring us a very high security. But, very sadly, this scenario never comes true. When rejected by biometrics, what can we do? We will only see that we are unable to login even if we can feed our password/PIN.
Hitoshi Kokumaiの記事
ブログを見る
Biometrics is 'probabilistic' by nature since it measures unpredictably variable body features of li ...
“Expanded Password System is no bad, but we do not need it. · We can rely on password managers that ...

Another topic for today is “Passwordless made simple with user empowerment” · https://www.securitym ...
この職種に興味がある方はこちら
-

事務職員
6日前
公開範囲1.等を含む求人情報を公開する Hirosaki, 日本 パート仕事内容 · 〇伝票入力 · 〇資材の在庫確認と発注 · 〇電話対応、来客対応 雇用形態 パート労働者 正社員登用の有無 あり 正社員登用の実績(過去3年間) 1名 派遣・請負等 就業形態 派遣・請負ではない 雇用期間 雇用期間の定めなし 就業場所 就業場所 事業所所在地と同じ 〒 青森県弘前市大字桜庭字清水流121番地1 最寄り駅 弘前駅 最寄り駅から就業場所までの交通手段 車 所要時間 40分 受動喫煙対策 あり(喫煙室設置) 受動喫煙対策に関する特記事項 ...
-

ネイリスト
2日前
MARIENAILS(マリーネイルズ)モザイクモール港北店 横浜市都筑区, 日本 正社員 アルバイト更新日: · 【業務内容】ネイリストとしてのサロンワーク業務全般 · 【雇用形態】 正社員 アルバイト · 【勤務地】横浜市営地下鉄「センター北駅」よりすぐネイルサロン · 【給与】【正社員】 · ■店長候補 · 月給 220,000円~+歩合 · ■サロンワーク経験2年以上 · 月給 200,000円~+歩合 · ■サロンワーク経験2年未満 · 月給 170,000円~+歩合 · 【アルバイト】 · ■サロンワーク経験2年以上 · 時給 1,112円~ · ■サロンワーク経験2年未満 · 時給 1,112円~ · 【試用期間中給与】【正社員】 · ■ ...
-

機械オペレーション(汎用・nc等)
1週間前
株式会社 綜合キャリアオプション 宇都宮店 塩谷郡高根沢町, 日本 TEMPORARY株式会社 綜合キャリアオプション 宇都宮店 · 高待遇★高時給★履歴書不要★ホースの原料補充・梱包/日払いOK · ====仕事内容==== · エアコンドレインホースの成型オペレーター原料補充、 · 梱包、 · その他付随する業務 · ≪当社の就業3大メリット≫ · ★給料日より前にお給料GET★ · 日払いOK支払い額は7割 · 即払いOKのオシゴトもあり · ★来社不要ノンストップで職場見学 · オンライン登録でスピード就業もOK · 就業までの接触機会の最小化を実現しました。 · ★交通費上限3万円業界トップクラス · 当社では働くあなたの負担を ...
コメント