Threat of Biometrics to Security and Its Structure
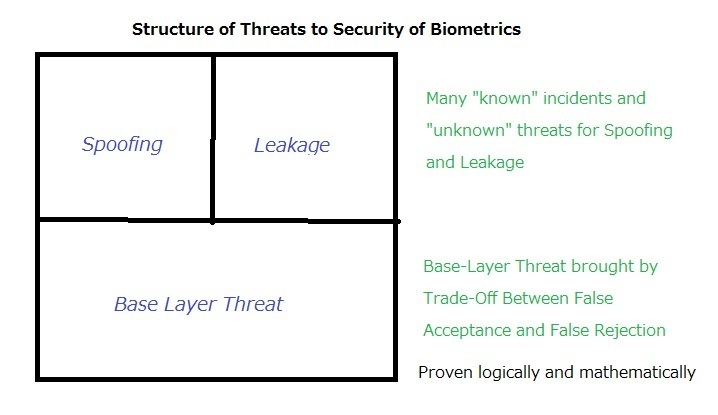
Threats of biometrics to privacy, democracy and humanity are already taken up by quite a few people, but not many people are discussing the threat to security of biometrics and many of them are often carried away by the eye-catching ”known” incidents of spoofing and leakage. Few people pay attention to the base-layer problem solidly inherent in the biometrics technology.
Assume an extremely unlikely scenario that someone comes up with a set of dream solutions by which there can be no spoofing and no leak of biometric data altogether. Even such a 'perfect biometrics' would only provide the level of security lower than a password/pincode-only authentication in cyberspace because biometrics needs to be deployed with a fallback measure (usually default password/pincode) against false rejection (false non-match) in a 'multi-entrance' deployment.
This peculiarity constitutes the base layer of the threat to security of biometrics. On top of this base layer, biometrics gives us additional layers of threats; spoofing and data leakage, which are supposed to haunt us for long in this real world.
By the way, as for the threats of spoofing and leakage, we need to assess both “known” incidents or precedents and “unknown” threats.
Just as the threat of man-made crimes should be assessed differently from the threat of natural disaster, new threats of ever-evolving digital crimes should be assessed differently from the time-honored threat of pre-digital crimes. If we have to wait for an incident or precedent to be “known to us” before we are allowed to discuss the threat, we would never be able to logically and mathematically identify the threat and prevent the identified threat from actually turning into an incident or precedent.
Whether a logical and mathematical reasoning of a potential threat is correct or wrong can only be tested logically and mathematically, not by whether it is known or not, whereas a physical phenomenon, for instance, whether this key fits into that lock or not could be tested physically.
Separately we could assess the threats of biometrics to the security of individual persons as well as that of the overall networks. Attacks on individuals must not be dismissed as a trivial matter.
Mr. A, for instance, is not wealthy so he can be confident that no bad guys would try to attack his accounts for money. He cannot be confident, however, that no bad guys would try to break into his accounts for personal revenge or harassment. He believes he has lived honestly, trying not to harm anyone. But it does not guarantee that he does not get hated. When his biometric data gets leaked, it could be an issue of life and death for him and his family.
And, it goes without saying that there are millions and millions of individuals who have money, power and influence that bad guys would not hesitate to spend their resources to pursue
Moreover, we know of the tragic events that actually happened – https://www.valuewalk.com/2018/02/biometrics-aadhaar-danger/
In this article we referred to an ill-thought deployment of biometrics with an explanation with graphs of what are false rejection and false acceptance.
As such, it is really sad to see so many people being (mis)led to believe that, although biometrics may be a threat to privacy, the biometrics must be supported by governments and citizens because biometrics contributes substantially to better security. This is a big myth that must be busted.
#identity #authentication #password #security #safety #biometrics #ethic #privacy #civilrights #democracy
Hitoshi Kokumaiの記事
ブログを見る
The quantum computer held in a bad guy’s hand is indeed a big threat. So is the artificial intellige ...
We’ve come up with a slide presentation for “Bring a healthy second life to your legacy password sys ...

I take up this new report today - “Researchers Defeated Advanced Facial Recognition Tech Using Makeu ...
関連プロフェッショナル
この職種に興味がある方はこちら
-

品出しスタッフ
1週間前
株式会社ベイシア 日光市, 日本 パートタイム株式会社ベイシア · 地元スーパーでフロアスタッフ《週3×4h》スキマ時間で働く&選べる働き方★未経験&扶養内OK★しゅふ活躍中・休日&時間帯加給あり・交通費支給 · ====仕事内容==== · ★働きやすさも、地域イチバン★ · 品質や価格はもちろん、働きやすさも地域イチバン · 近所のスーパー《ベイシア》で一緒に働きませんか? · 業務はそれぞれの担当制。 · スーパーを利用したことのある方なら、働くイメージもわきやすく · 未経験でもリラックスしてスタートできますよ♪ · \BM販売スタッフ業務/ · 【仕事詳細】 · 商品陳列・補充、レジチェッ ...
-
Nojima Corporation Kawasaki, 日本仕事情報 · ● 仕事内容 ご案内する商品は、テレビ、レコーダー、オーディオ機器やエアコン・扇風機・暖房機器などの季節家電季節や気候に応じてお客様のお話を聞いて、最適な商品の提案をお願いします。ノルマがないのも働きやすさのポイントお客様との関わりを大切にしながら働ける環境です。 ●9割が未経験スタート 接客や販売が始めての方も手厚いわかりやすい研修があるので、安心してご応募下さい。異業種からの転職者も多数活躍中研修や日々の仕事でマナー、コミュニケーション力などスキルが身に付きます。関東圏や静岡県を中心に265店舗以上展開する東証一部上場企業のノジマで一 ...
-
甲南医療センター-4469
5日前
エームサービスジャパン株式会社 Kobe, 日本仕事情報 · ● 仕事内容 栄養士、管理栄養士として、入院患者さんの健康状態に応じた · 栄養管理、食べやすさ、味や盛り付けにもこだわり、調理・配膳 · 下膳から食品の発注・在庫管理、食材選びやメニュープランまで · かかわっていただきます。ただ食事を提供するだけではなく、 · 患者さんの楽しみや回復につながる重要なお仕事です。 ●病院食は治療の一環 病院の食事は治療の一環となる大切なもの。 · 適温適時・選択食を含む付加価値の提供を目指しています。 · 患者様一人ひとりの病態などに合わせた質の高い治療食などにも · 工夫を凝らし、オリジナルレシピや新 ...


コメント
Debesh Choudhury
4年前 #1